

…For now. Looks like they’re going to get rid of it too (which makes sense, because they copy Chromium’s codebase).
https://learn.microsoft.com/en-us/microsoft-edge/extensions-chromium/developer-guide/manifest-v3


…For now. Looks like they’re going to get rid of it too (which makes sense, because they copy Chromium’s codebase).
https://learn.microsoft.com/en-us/microsoft-edge/extensions-chromium/developer-guide/manifest-v3


I think that’s the point: Google has been shutting down Manifest V2 extensions one step at a time, and it’s been experimenting with anti-ad-block tech on YouTube with one user group at a time.
disingeneous to call it adding ads
Who called it adding


With all due respect, Mozilla is now (and, for a while, has been) an ad company. When an ad company tells you ads are necessary, you should not trust them. Plenty of lousy things have been entrenched as social norms, but it is the job of the entrenchers to justify their existence… Which Mozilla is definitely not doing here.
Brave can keep the old APIs but they’ll still be affected, because developers for Chromium-compatible browsers still have to decide whether they want to create or support apps that will only work in a subset of browsers, and figure out how to distribute them outside the Chromium store.
TIL the things to build a browser take up less space than a package manager… But I don’t do Linux any more hardcore than Ubuntu either


Corrupt politicians can simply ignore the law. If they didn’t ignore it, they wouldn’t be very corrupt.
Telegram hasn’t been secure since basically day 1. IIRC it went something like
Security experts: Never roll your own cryptography.
Telegram: We rolled our own cryptography!
Security experts: Don’t. And it’s broken.
Telegram: uhhhh… We fixed it.
Security experts: It still looks really bad. Stop it.
Telegram: says nothing
I want Mozilla to make a browser that preserves privacy. They keep making it worse. And I don’t see how giving them money is helping them improve.
And my comment won’t cost them any money either, as @[email protected] pointed out:
Plus donations to Mozilla cannot even be used for Firefox development due to the structure of the foundation and corporation.
I don’t think Mozilla should be deprived of money, and Firefox (or a lightly modified fork like Librewolf) is and probably always will be my default browser… But they’re getting plenty of money from elsewhere, so they probably don’t need ours.
I would encourage people to withhold donations from Mozilla. They have plenty of money rolling in, and in the past year they used it to overpay their CEO disproportionately, and to buy an AdTech company with private data that they sell.
https://en.wikipedia.org/wiki/Mitchell_Baker#Negative_salary-performance_correlation
https://www.fakespot.com/privacy-policy (search “personal information is sold”)
Update: Apple’s role in adding extra location data to your request has been added to this post
Apple and a couple other providers have been experimenting with a multi-hop system of making your connections private.
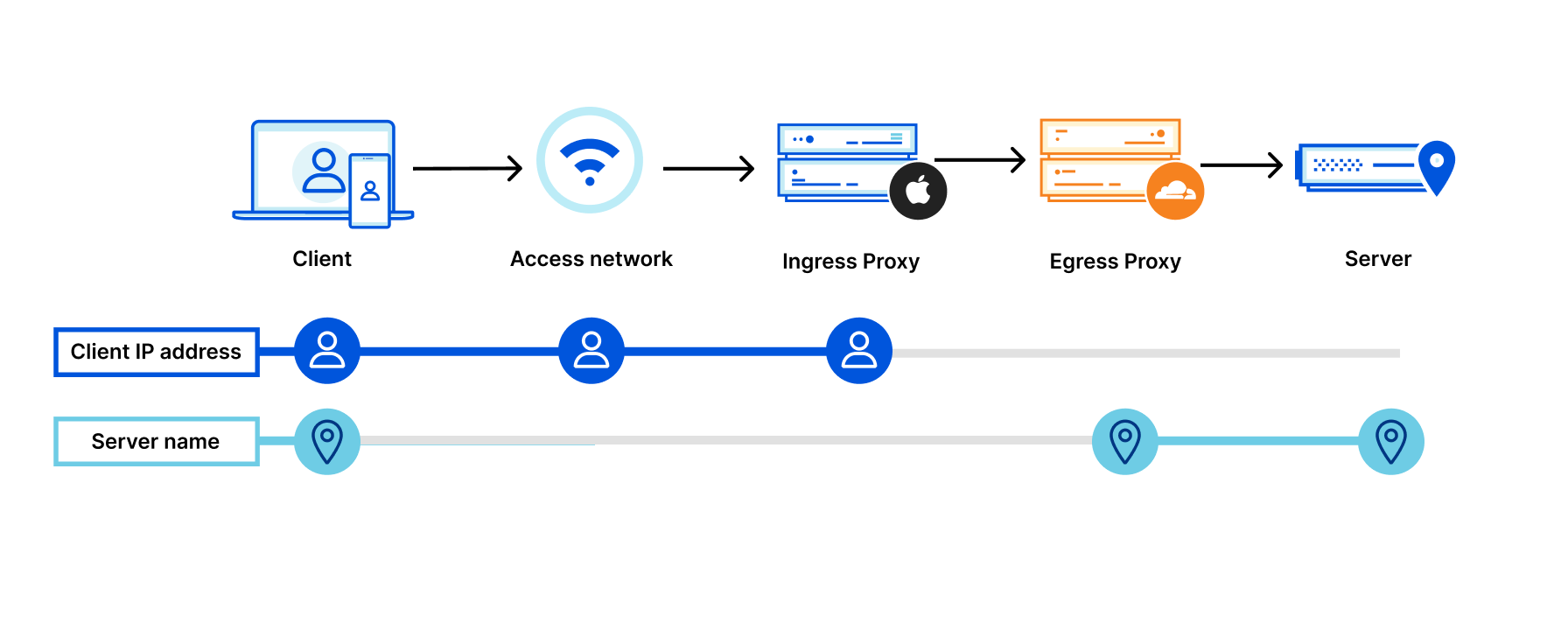
Here’s what a competitor, Invisiv, says.
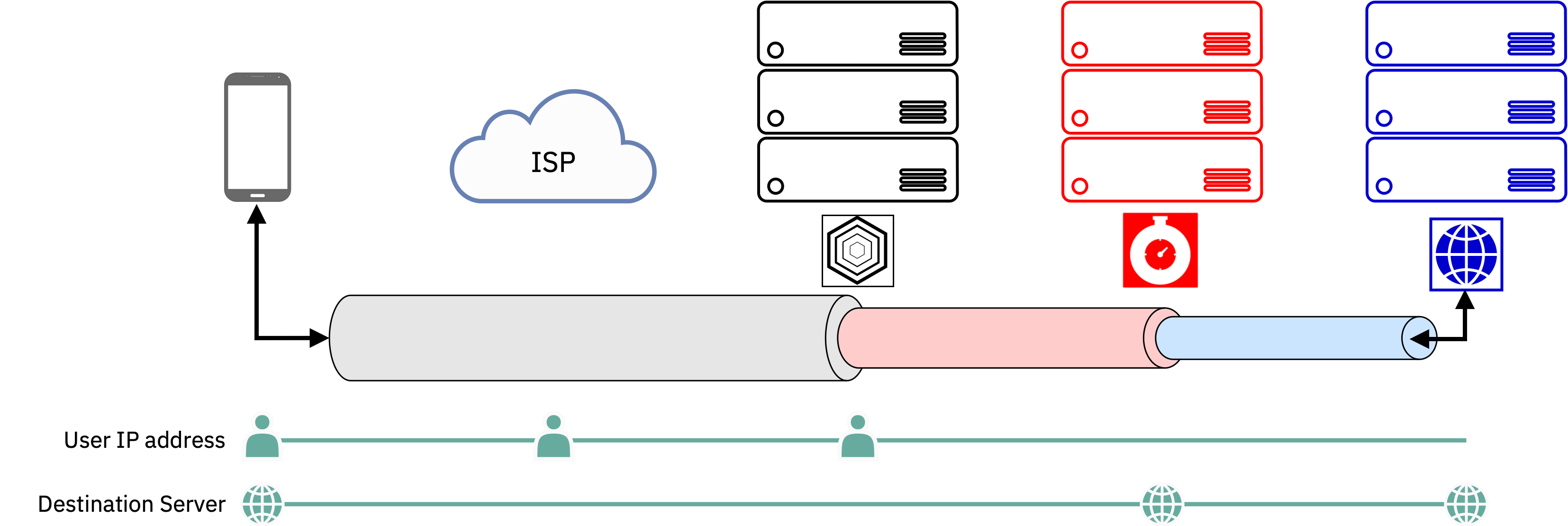
Both pages are pretty hard to parse (IMO Cloudflare uses more jargony language: “ingress”/“egress server” - really?) but they get to the same point.
Your data takes a path like this
The obvious issues here:
In the case of Apple/Cloudflare, reputation is rather poor. From PRISM to false advertising to notification telemetry, Apple hasn’t exactly delivered on their promise. In terms of Invisiv, the company has some big names on board but Fastly and Cloudflare both have a rather significant grip on the internet (with Cloudflare’s being bigger) but any CDN gets a good view into personal data most of the time.
Update: in the case of Cloudflare/Apple, Apple adds additional location data to your request, making its “private” relay leak approximate location data the same way your IP address could leak it. To wit:
Apple relays geolocate user IP addresses and translate them into a “geohash”. Geohashes are compact representations of latitude and longitude.
But on the bright side: a VPN has far more issues than either of these, as it’s basically #4 above except the same service also has your identity by necessity. An untrustworthy VPN is as harmful as an untrustworthy ISP, with very little separating them.
Acceptable Ads is bullshit on many levels:
uBlock Origin, or at least uBlock Origin Lite on Chromium-like browsers, are must-haves.
The best browser you can set up for a family member, IMO, is Firefox. Disable Telemetry (which should rid them of Mozilla’s own ad scheme too), install uBlock Origin, remind them to never call or trust any other tech support people who reach out to them, and maybe walk them through some scam baiting videos.
I’m still evaluating which Chrome-likes are best at actual ad blocking, and the landscape is grim.